|
from Alice’s Adventures in Wonderland, Lewis Carroll Alice holds the key. |
1. Manual Pages
2. Table of Contents
3. Synopsis
ntpkeygen[-V]
4. Description
This program generates a file containing keys that can be used in NTP’s symmetric key cryptography.
The program produces a file containing ten pseudo-random printable ASCII strings suitable for the MD5 message digest algorithm. It also produces an additional ten hex-encoded random bit strings suitable for the SHA-1 and other message digest algorithms.
The keys file must be distributed and stored using secure means
beyond the scope of NTP itself. The keys can also be used as
passwords for the ntpq utility program.
5. Command Line Options
-V,--version-
Print the version string and exit.
6. Running the program
The simplest way to run the ntpkeygen program is logged in directly as
root. The recommended procedure is to change to the keys directory,
usually /etc/ntp/, then run the program. Then chown the output
file to ntp:ntp. It should be mode 400.
|
Warning
|
ntpkeygen uses the system randomness source. On a POSIX
system, this is usually /dev/urandom. Immediately after a reboot, on any
OS, there may not be sufficient entropy available for this program to
perform well. Do not run this program from any startup scripts. Only
run this program on an active host with a lot of available entropy.
|
7. Key file access and location
File names begin with the prefix ntpkey and end with the postfix hostname.filestamp, where hostname is the owner name, usually the string returned by the Unix gethostname() routine, and filestamp is the NTP seconds when the file was generated, in decimal digits.
ntpkeygen also makes a soft link from ntp.keys to the generated
file. ntp.keys is the normal file used in ntp.conf.
8. Random Seed File
All key generation schemes must have means to randomize the entropy seed used to initialize the internal pseudo-random number generator used by the library routines.
It is important to understand that entropy must be evolved for each generation, for otherwise the random number sequence would be predictable. Various means dependent on external events, such as keystroke intervals can be used to do this and some systems have built-in entropy sources.
This implementation uses Python’s random.SystemRandom class, which relies on os.urandom(). The security of os.urandom() is improved in Python 3.5+.
9. Cryptographic Data Files
Unlike NTP Classic, this implementation generates only AES keys, not MD5 or SHA1.
Since the file contains private shared keys, it should be visible only to root or ntp.
In order to use a shared key, the line to be used must also be setup on the target server.
This file is also used to authenticate remote configuration commands used by the ntpq(1) utility.
Comments may appear in the file and are preceded with the #
character.
Following any headers the keys are entered one per line in the format:
| Field | Meaning |
|---|---|
keyno |
Positive integer in the range 1-65,535 |
type |
Type of key (MD5, SHA-1, AES-CMAC etc). This program generates only AES. |
key |
the actual key, printable ASCII or hex |
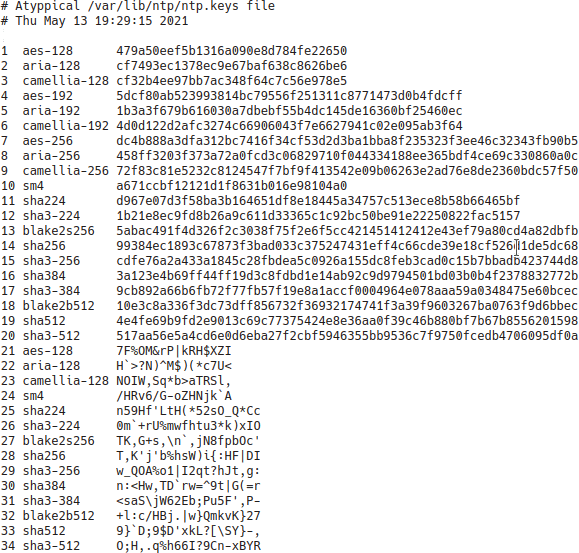
Figure 1. Typical Symmetric Key File
Figure 1 shows a typical symmetric keys file used by the reference
implementation. Each line of the file contains three fields, first
keyno an integer between 1 and 65535, inclusive, representing the
key identifier used in the server configuration commands. Next
is the key type for the message digest algorithm, which can be any
message digest algorithm supported by the OpenSSL library.
For details, see ntp.keys(5).
ntpkeygen just makes a sample file with good random keys. You can
edit it by hand to change the keyno or keytype and/or copy lines to
other key files.
